10 security-by-design principles to include in the SDLC
Table Of Content
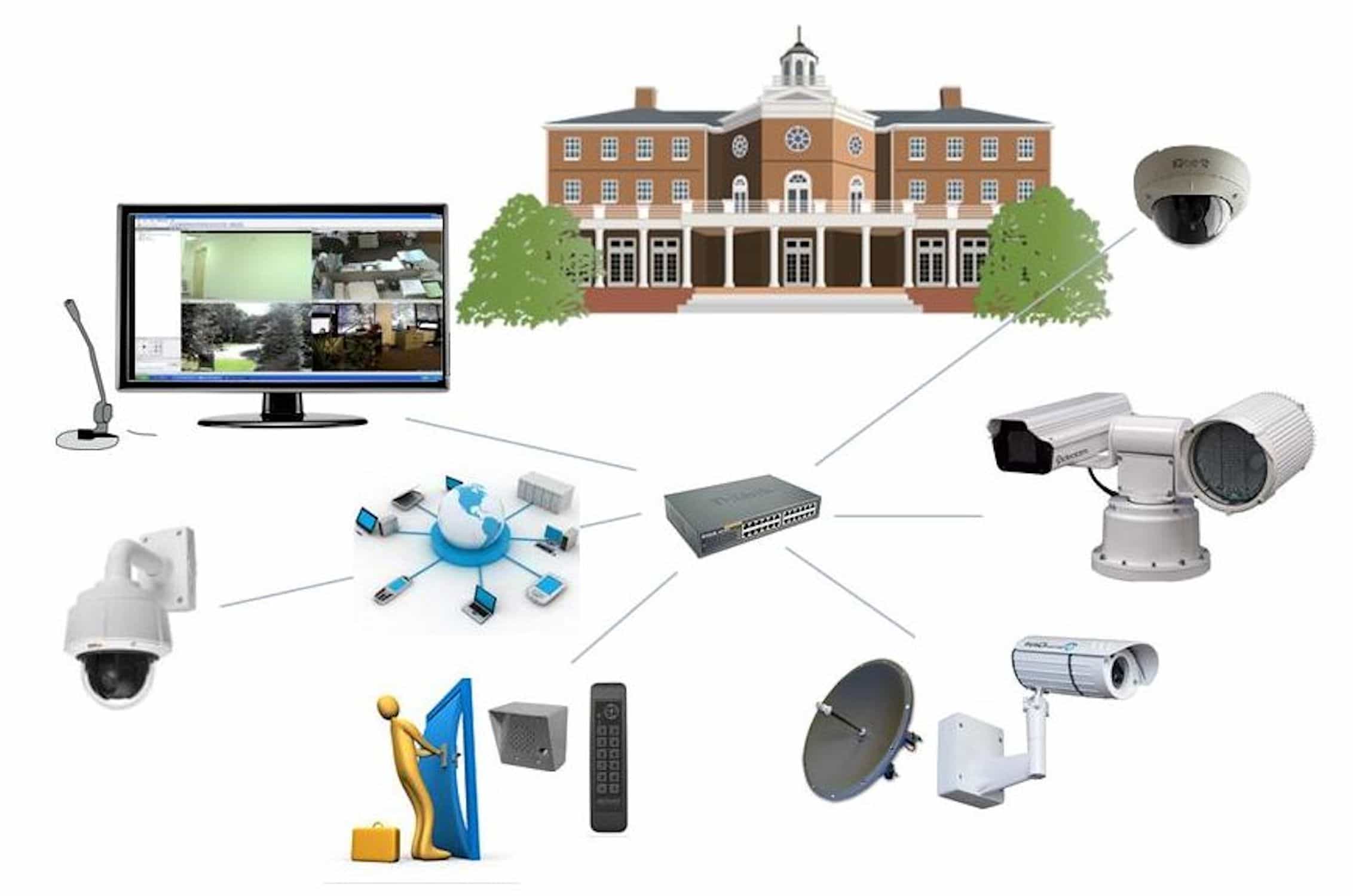
Basic resilience starts with data backups and redundancy for key components such as firewalls, routers, and data servers. Basic DDoS protection and load balancers also will be early controls applied to protect websites, application servers, and key networks. Basic centralized control deploys management modules for network equipment and firewalls for centralized management of existing infrastructure.
Technology Solutions Provider
Secure by Design Alert: Security Design Improvements for SOHO Device Manufacturers - CISA
Secure by Design Alert: Security Design Improvements for SOHO Device Manufacturers.
Posted: Wed, 31 Jan 2024 08:00:00 GMT [source]
Technology manufacturers must increasingly embrace their role in putting consumer safety first. Technology providers and software developers must take the first step to shift this burden by claiming ownership of their customers’ security outcomes. The Wall Street Journal reported Monday that the criminal hacking affiliate of ALPHV broke into Change Healthcare’s network using stolen credentials for a system that allows remote access to its network.

Principle: Least privilege
Your body may have a lot of different parts, but put together, they are a system of systems that work together and help you get through your daily life. As part of that daily grind, our bodies have methods of protection, namely by using systems in tandem. While the AWS Security by Design framework is focused on AWS workloads, its principles can be applied to any cloud or noncloud workload, regardless of platform. Much of the U.S. healthcare system ground to a halt, with healthcare providers facing financial pressure as backlogs grow and outages linger.
TechnologySolutions Provider
Economic designs maximize the value of the components and minimize costs through simplicity. Reductions in attack surface similarly reduce monitoring costs and complexity. Additionally, economic designs boost operations data throughput to maintain high availability. Advanced centralized control will manage local, remote, and cloud resources through unifying technology such as SD-WAN, SASE, or SSE. The most sophisticated organizations will also consider centralized and more granular zero trust implementations. Initial iterations for improvement can start annually, but quarterly or more frequently tends to be a more reasonable update cadence.
Repository for Software Attestations and Artifacts (RSAA) User Guide
Examine existing controls, operations, and security processes for opportunities to gain time and reduce expenses through simplification and consolidation. Basic defense in depth applies multiple controls starting with key, high-value assets and adding others as budgets and time allow. For example, in addition to the existing security stack, a data center might add additional MFA, a web application firewall, and a honeypot. Advanced cybersecurity training utilizes more active training for security professionals and relevant non-security employees. Use table top exercises or simulated attacks (red, blue, or purple teaming) to gain valuable experience and test controls and processes under stress. Ali thinks secure-by-design is not only about software but also about building systems the right way.
The Security-by-Design Approach
Security 101 – Los Angeles is now recruiting a Lead Commercial Security Technician that has experience installing programming and servicing commercial electronic security devices primarily IP network systems and overall security systems. A global technology consulting firm that leverages design thinking, interdependent subject matter expertise, and emerging technology solutions to help organizations achieve meaningful transformation. Define your requirements, design the right architecture, and deploy solutions that integrate with your business process. ESecurity Planet is a leading resource for IT professionals at large enterprises who are actively researching cybersecurity vendors and latest trends.
Let us educate and train your team on how to maintain security and mitigate future risks. The startup’s founders also want to create tools to monitor and block software such as cryptocurrency miners and ransomware. What we need is to actually take the tools available and put them in the right place,” Sosonkin said. Experience 24/7 site protection that's not just smart but intuitive, proactively detecting threats, dynamically intercepting them, and strategically preventing future incidents.
Department of Defense (US) Architecture Framework (DoDAF)
The admission that hackers stole Americans’ health data comes a week after a new hacking group began publishing portions of the stolen data in an effort to extort a second ransom demand from the company. Health insurance giant UnitedHealth Group has confirmed that a ransomware attack on its health tech subsidiary Change Healthcare earlier this year resulted in a huge theft of Americans’ private healthcare data. We offer experienced support, nimble delivery times, and customized engagements for your business. The two different arrangements of camera lenses for the Pro and Vanilla handsets are clear. All four models now have a vertical arrangement of two lenses, an arrangement made to support the recording of spatial videos that can play back in the Apple Vision Pro in 3D.
Our Penetration Testing team will simulate real-world adversarial attacks on your networks, wireless solutions, applications, systems and devices. The DoubleYou team wants to use techniques frequently used by hackers to attack Apple systems to apply them as defense tools. The researchers say they’re developing a method for analyzing all macOS processes to detect and block any untrusted code, as well as monitoring and blocking anomalies in DNS traffic.
Network security architecture goals define what to do, but best practices offer guidance on how to implement those goals effectively. Best practices address one or more goals and will reinforce other best practices, starting with iterative planning. Others seek centralized control, employee training, defense in depth, efficient design, least privilege access, resilience, and testing.
The Principle of Least Privilege (POLP) states that a user should have the minimum set of privileges required to perform a specific task. That search feature is potentially vulnerable to file inclusion attacks and SQL injection attacks. STRIDE helps programmers identify threats and DREAD allows programmers to rate threats.
Cybersecurity training ensures effective controls throughout the organization. General employee training creates a security-oriented organization aware of key threats and trends. Specific training on security tools reduces barriers to adoption and improves their effectiveness. Effective controls require security measures that work as intended, consistently over time. Implement usable security controls that prevent bypass, circumvention, or tampering without compromising other network security architecture goals.
Effective centralized control puts critical decisions into the hands of experts and delivers consistent results throughout the network and its attached assets. This goal requires effective disaster recovery plans to recover corrupted data as well as scalability and redundancy of systems for continuous availability during high demand. There are many reasons why a web application would fail to process a transaction. Perhaps a database connection failed, or the data inputted from a user was incorrect. So, instead of having one security control for user access, you would have multiple layers of validation, additional security auditing tools, and logging tools.
Our work in Red Hat Product Security is to help minimize the software-based risks of enterprise open source from Red Hat, while affording the many benefits that open source can provide. A cybersecurity mesh architecture solution that provides a real-time view of compliance and business risk. For more specialized network security architecture information, consider reading about cloud security best practices and tips. The Sherwood Applied Business Security Architecture (SABSA) helps to design, deliver, and support security services for risk management and information assurance. The dedicated SABSA Institute manages ongoing development, training, and certification.
Advanced iterative planning formally integrates risk registers or risk management tools into the process. Governance, risk, and compliance (GRC) tools help to prioritize the most valuable or the most damaging data and systems for additional layers of protection. Components of economic design include virtualization to maximize asset utilization, simplifying into easy-to-test components, and attack surface minimization. Security by design is an approach in development that helps to focus on making software as secure as possible already in the development process. OWASP suggests that programmers create security controls that are appropriate for the value of the data being managed. For example, an application processing financial information must have much tighter restrictions than a blog or web forum.
Comments
Post a Comment